Spoofing Attack Network Projects prevent malicious user access in any network by apt verification. In common, the spoofing attack attempts to impersonate legitimate identification to take part in the network. Spoofing Attack Network attack, the malicious node or user gains legitimate access through falsifying some information. By and large, this info belongs to a number of types.
The above list, IP Spoofing is common in all networks. In that, the attacker creates IP packets with the false address by impersonating a valid address. As we all know, all of the current wireless networks are IP based. It means that all networks are at risk of this attack. Mainly, it also affects the real-time use cases.
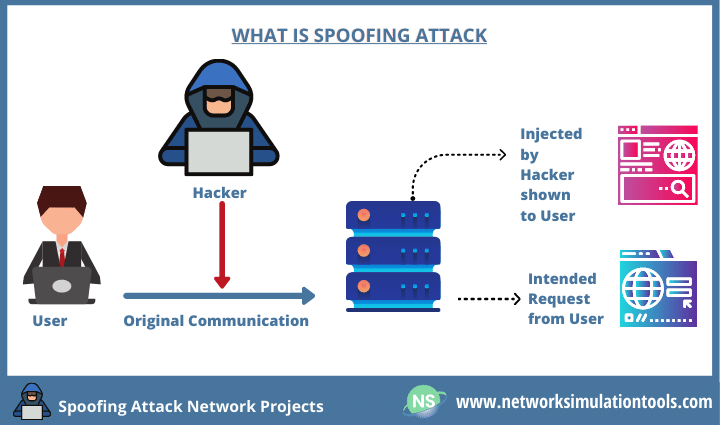
On top, our Spoofing Attack Network Projects resolve this attack by keen methods. In chief, it leads to DDoS and other attacks too. And also, this attack carries through Authentication, Network Routing Info, and Emergency Messages. Thus, its severity is on the top of the network.
Usually, we can cope with this attack in three stages. Each stage has an individual aim to defend against a spoofing attack.
To mention the fact, we have versatile skills in all the above stages. That is to say; we have the ability to endow a full-fledged project for you based thesis on wireless networks. Without a doubt, you will gain an A+ grade in your career as we bring not only a project but also fine training during the course of your journey. From top to bottom, we give apt help at the needy time.
In sum, you will turn into an expert in your field with our help. It is not a statement; it is our vision to see all our students as experts. With us, you will find an easy way to reach the top. But we will not define your limits.
| Technology | Ph.D | MS | M.Tech |
|---|---|---|---|
| NS2 | 75 | 117 | 95 |
| NS3 | 98 | 119 | 206 |
| OMNET++ | 103 | 95 | 87 |
| OPNET | 36 | 64 | 89 |
| QULANET | 30 | 76 | 60 |
| MININET | 71 | 62 | 74 |
| MATLAB | 96 | 185 | 180 |
| LTESIM | 38 | 32 | 16 |
| COOJA SIMULATOR | 35 | 67 | 28 |
| CONTIKI OS | 42 | 36 | 29 |
| GNS3 | 35 | 89 | 14 |
| NETSIM | 35 | 11 | 21 |
| EVE-NG | 4 | 8 | 9 |
| TRANS | 9 | 5 | 4 |
| PEERSIM | 8 | 8 | 12 |
| GLOMOSIM | 6 | 10 | 6 |
| RTOOL | 13 | 15 | 8 |
| KATHARA SHADOW | 9 | 8 | 9 |
| VNX and VNUML | 8 | 7 | 8 |
| WISTAR | 9 | 9 | 8 |
| CNET | 6 | 8 | 4 |
| ESCAPE | 8 | 7 | 9 |
| NETMIRAGE | 7 | 11 | 7 |
| BOSON NETSIM | 6 | 8 | 9 |
| VIRL | 9 | 9 | 8 |
| CISCO PACKET TRACER | 7 | 7 | 10 |
| SWAN | 9 | 19 | 5 |
| JAVASIM | 40 | 68 | 69 |
| SSFNET | 7 | 9 | 8 |
| TOSSIM | 5 | 7 | 4 |
| PSIM | 7 | 8 | 6 |
| PETRI NET | 4 | 6 | 4 |
| ONESIM | 5 | 10 | 5 |
| OPTISYSTEM | 32 | 64 | 24 |
| DIVERT | 4 | 9 | 8 |
| TINY OS | 19 | 27 | 17 |
| TRANS | 7 | 8 | 6 |
| OPENPANA | 8 | 9 | 9 |
| SECURE CRT | 7 | 8 | 7 |
| EXTENDSIM | 6 | 7 | 5 |
| CONSELF | 7 | 19 | 6 |
| ARENA | 5 | 12 | 9 |
| VENSIM | 8 | 10 | 7 |
| MARIONNET | 5 | 7 | 9 |
| NETKIT | 6 | 8 | 7 |
| GEOIP | 9 | 17 | 8 |
| REAL | 7 | 5 | 5 |
| NEST | 5 | 10 | 9 |
| PTOLEMY | 7 | 8 | 4 |