Byzantine Attack Network Projects take immediate action on all kinds of threats. The byzantine attack is one of the most dangerous attacks. First of all, this attack turns a set of normal nodes into malicious in any network. Next, the attacker takes control over the network by this set of nodes. In the point of fact, this set of nodes act as the selfish nodes in the network. At last, it enables actions including Packet Drop, Redirection, and so on. As it targets to control the entire network, it degrades the overall performance.
And more all aforesaid networks are at utmost risk of byzantine attack. As all these networks are application-specific, they need great attention. With this in mind, we bring novel Byzantine Attack Network Projects in real-time too.
In simple, the byzantine attack has a multi-level of severity. On account of this fact, it demands multiple parameters to find the severity. We defined these parameters for your info here.
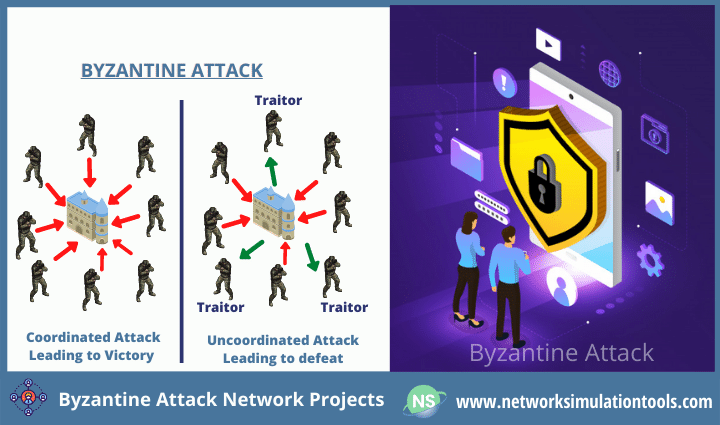
When the severity level is open, then it is easy to mitigate the attack. Unlike other threats, cryptography algorithms are in short supply to this attack. The key method is to find the mean nodes in the network.
This info is the base to compute the trust value of a node. Based on the trust value, we can secure the network processes from attack. For a case, Route selection with trusted nodes will resolve the problem of excess packet drop. On top of the trust value, a number of countermeasures are there.
We have intense insights into all of the algorithms and methods in cryptography based projects. So, you can join us without a doubt. Our frequent notices will help you to track the project status. In other words, we keep your project nearer to you. With us, you will gain much more wisdom to grow up your skills. To sum up, we will bear you huge feats even with your small efforts.
| Technology | Ph.D | MS | M.Tech |
|---|---|---|---|
| NS2 | 75 | 117 | 95 |
| NS3 | 98 | 119 | 206 |
| OMNET++ | 103 | 95 | 87 |
| OPNET | 36 | 64 | 89 |
| QULANET | 30 | 76 | 60 |
| MININET | 71 | 62 | 74 |
| MATLAB | 96 | 185 | 180 |
| LTESIM | 38 | 32 | 16 |
| COOJA SIMULATOR | 35 | 67 | 28 |
| CONTIKI OS | 42 | 36 | 29 |
| GNS3 | 35 | 89 | 14 |
| NETSIM | 35 | 11 | 21 |
| EVE-NG | 4 | 8 | 9 |
| TRANS | 9 | 5 | 4 |
| PEERSIM | 8 | 8 | 12 |
| GLOMOSIM | 6 | 10 | 6 |
| RTOOL | 13 | 15 | 8 |
| KATHARA SHADOW | 9 | 8 | 9 |
| VNX and VNUML | 8 | 7 | 8 |
| WISTAR | 9 | 9 | 8 |
| CNET | 6 | 8 | 4 |
| ESCAPE | 8 | 7 | 9 |
| NETMIRAGE | 7 | 11 | 7 |
| BOSON NETSIM | 6 | 8 | 9 |
| VIRL | 9 | 9 | 8 |
| CISCO PACKET TRACER | 7 | 7 | 10 |
| SWAN | 9 | 19 | 5 |
| JAVASIM | 40 | 68 | 69 |
| SSFNET | 7 | 9 | 8 |
| TOSSIM | 5 | 7 | 4 |
| PSIM | 7 | 8 | 6 |
| PETRI NET | 4 | 6 | 4 |
| ONESIM | 5 | 10 | 5 |
| OPTISYSTEM | 32 | 64 | 24 |
| DIVERT | 4 | 9 | 8 |
| TINY OS | 19 | 27 | 17 |
| TRANS | 7 | 8 | 6 |
| OPENPANA | 8 | 9 | 9 |
| SECURE CRT | 7 | 8 | 7 |
| EXTENDSIM | 6 | 7 | 5 |
| CONSELF | 7 | 19 | 6 |
| ARENA | 5 | 12 | 9 |
| VENSIM | 8 | 10 | 7 |
| MARIONNET | 5 | 7 | 9 |
| NETKIT | 6 | 8 | 7 |
| GEOIP | 9 | 17 | 8 |
| REAL | 7 | 5 | 5 |
| NEST | 5 | 10 | 9 |
| PTOLEMY | 7 | 8 | 4 |