Hashing Algorithm Projects highlight the key points of hashing algorithms. Also, it shows the pros and cons of hashing algorithms. Hashing is a cryptographic technique that purpose is to hide the data before sending it to the final point. Here, the hash values created for inputs data. In general, we all know that no one will access private data. For that, we secure data before going to transmit. The purpose of hashing is to ensure data integrity. Let’s check the most important and ideal features to choose the apt hashing algorithm.
Authentication is an essential issue to protect the user’s credentials. When authentication failed, it makes the intruder trace the original user’s security attributes or data. At first, hash values are computed. Then it is stored in a secure medium. Next, hash values are computed and compared with the original inputs. If both are matched, then the input considers as Authentic. When it does not match, then the particular request has been denied. For instance, image authentication by hashing must preserve from the following.
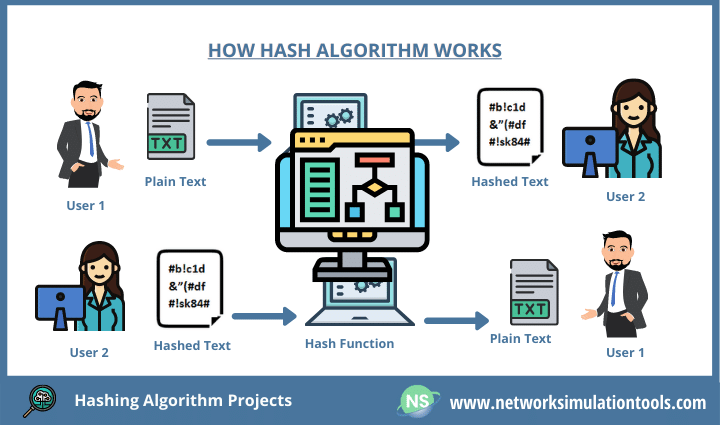
As you can see above, we have a long list of algorithms. To clarify, it transforms any kind of inputs into hash values. Each method has pros and cons in Visual Cryptography Projects. That is to say; the SHA family is better than MD5. Now, MD5 is totally compromised by intruders.
In order to safer against many attacks, we have two options. The first option is to detect the attackers by their behaviors. Another one is to prevent it. In truth, prevention is better rather than detection. For this event, we list a few latest functions. So far, we use the recent method for a project. Besides, after knowing the pros and cons, only we apply it in the hashing algorithm projects.
Overall, we give you the worthy content to start up your network project guidance. In fact, we work for nearly 40K ideas with security concepts. On top, we define the high range of info of the hashing area as we keep an eye on IEEE to update our minds with novel ideas. Nearly 92+ subjects we cover and work for students on each day. To be sure, if you want to know vast, we lend our aid. To sum up, we do not put an infinite symbol when you work with us for a great dream and get a smiley feel.
| Technology | Ph.D | MS | M.Tech |
|---|---|---|---|
| NS2 | 75 | 117 | 95 |
| NS3 | 98 | 119 | 206 |
| OMNET++ | 103 | 95 | 87 |
| OPNET | 36 | 64 | 89 |
| QULANET | 30 | 76 | 60 |
| MININET | 71 | 62 | 74 |
| MATLAB | 96 | 185 | 180 |
| LTESIM | 38 | 32 | 16 |
| COOJA SIMULATOR | 35 | 67 | 28 |
| CONTIKI OS | 42 | 36 | 29 |
| GNS3 | 35 | 89 | 14 |
| NETSIM | 35 | 11 | 21 |
| EVE-NG | 4 | 8 | 9 |
| TRANS | 9 | 5 | 4 |
| PEERSIM | 8 | 8 | 12 |
| GLOMOSIM | 6 | 10 | 6 |
| RTOOL | 13 | 15 | 8 |
| KATHARA SHADOW | 9 | 8 | 9 |
| VNX and VNUML | 8 | 7 | 8 |
| WISTAR | 9 | 9 | 8 |
| CNET | 6 | 8 | 4 |
| ESCAPE | 8 | 7 | 9 |
| NETMIRAGE | 7 | 11 | 7 |
| BOSON NETSIM | 6 | 8 | 9 |
| VIRL | 9 | 9 | 8 |
| CISCO PACKET TRACER | 7 | 7 | 10 |
| SWAN | 9 | 19 | 5 |
| JAVASIM | 40 | 68 | 69 |
| SSFNET | 7 | 9 | 8 |
| TOSSIM | 5 | 7 | 4 |
| PSIM | 7 | 8 | 6 |
| PETRI NET | 4 | 6 | 4 |
| ONESIM | 5 | 10 | 5 |
| OPTISYSTEM | 32 | 64 | 24 |
| DIVERT | 4 | 9 | 8 |
| TINY OS | 19 | 27 | 17 |
| TRANS | 7 | 8 | 6 |
| OPENPANA | 8 | 9 | 9 |
| SECURE CRT | 7 | 8 | 7 |
| EXTENDSIM | 6 | 7 | 5 |
| CONSELF | 7 | 19 | 6 |
| ARENA | 5 | 12 | 9 |
| VENSIM | 8 | 10 | 7 |
| MARIONNET | 5 | 7 | 9 |
| NETKIT | 6 | 8 | 7 |
| GEOIP | 9 | 17 | 8 |
| REAL | 7 | 5 | 5 |
| NEST | 5 | 10 | 9 |
| PTOLEMY | 7 | 8 | 4 |