Time needed: 5 minutes
Follow from Step 1 to Step 7 in order to create Contiki projects. Quick guide to create Security Protocol in Contiki . Reach us , if you want an customize Contiki projects works for scholars.
Symmetric encryption is one of a type of encryption. By use where only one key is used to both encrypt and decrypt electronic information. For make a secure purpose we make a communication between the entities/nodes via symmetric encryption . During the process must exchange the key so that it can be used in the decryption process.
Some examples of symmetric encryption algorithms include:
• AES (Advanced Encryption Standard)
• DES (Data Encryption Standard)
• IDEA (International Data Encryption Algorithm)
• Blowfish (Drop-in replacement for DES or IDEA)
• RC4 (Rivest Cipher 4)
• RC5 (Rivest Cipher 5)
• RC6 (Rivest Cipher 6)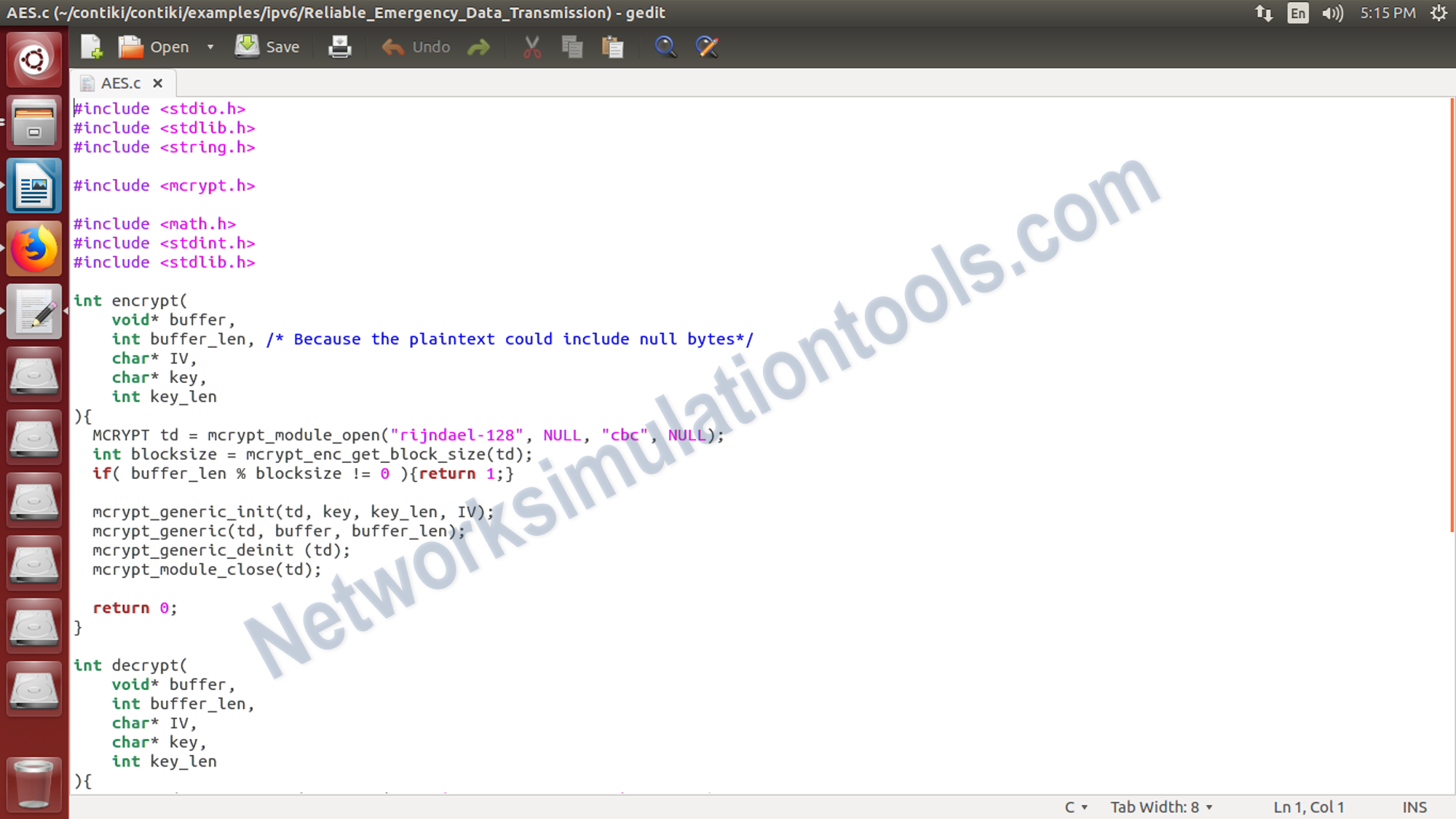
Asymmetric cryptography is a process of cryptography where a secret key can be divided into two parts,like a public key and a private key. The public key can be access by anyone, the user may be trusted or not, while the private key must be kept secret. And also the Asymmetric cryptography has two primary use cases: authentication and confidentiality. By using asymmetric cryptography, messages are create as a signature with a private key, and then anyone with the public key is able to verify that the message .
The sample list of sample algorithms are,
RSA Asymmetric Encryption Algorithm
ECC Asymmetric Encryption Algorithm
The hybrid encryption technique is used in applications such as SSL/TLS certificates. SSL/TLS encryption is applied during a series of perform the communications between servers and clients. During the communication we identity of both parties is verified using the private and public key. Once both parties have confirmed their identities, the encryption of the data takes place through symmetric encryption using session key.
Protocols in the cooja tool
for example , we will implement the AES algorithm.
Initially,Next open the terminal by press ctrl+alt+T buttons or search from the installed software list.
Change the contiki installation location in the terminal, using the command cd contiki/tools/cooja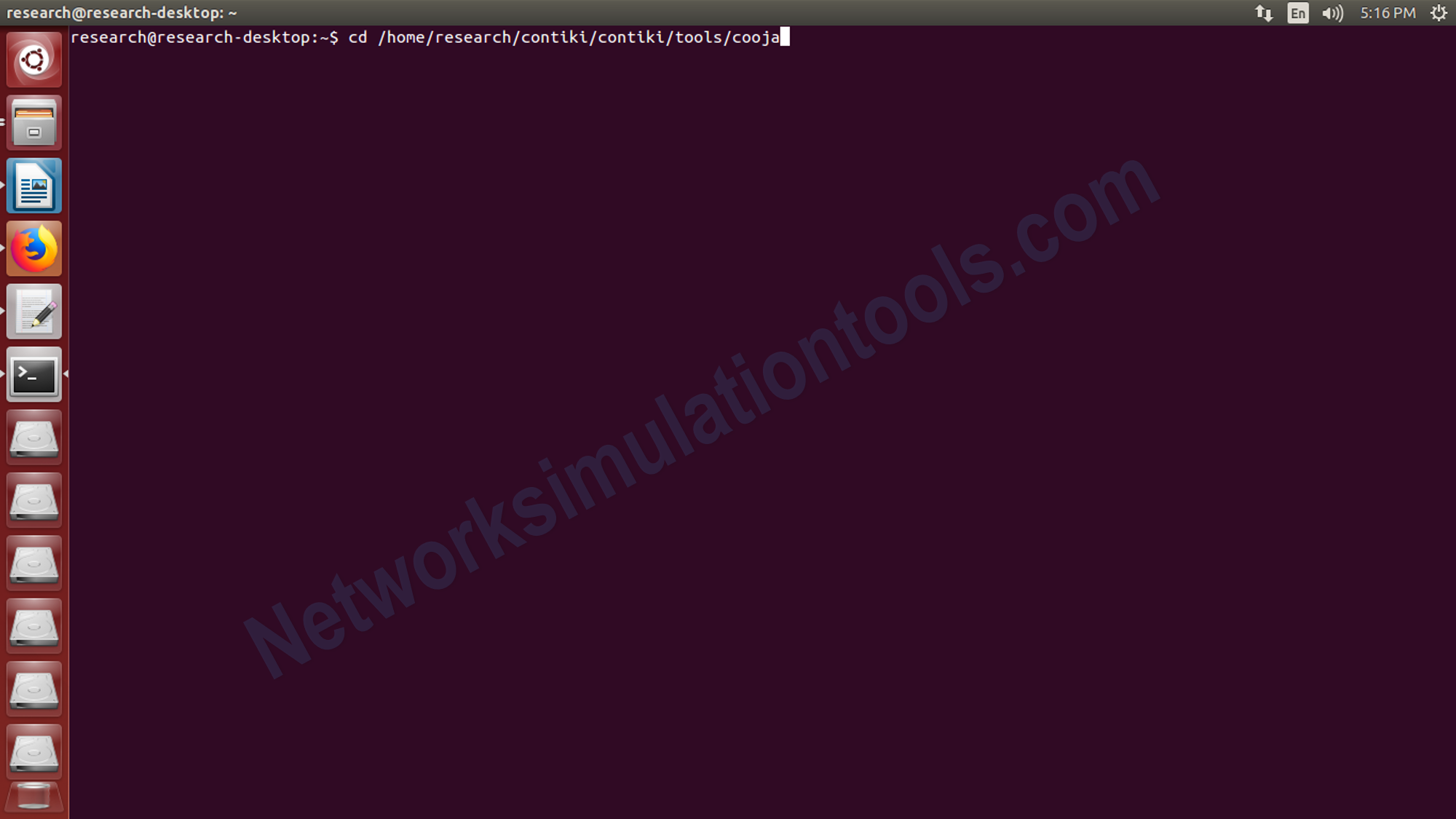
For get the simulation , execute the command ant run , in the terminal
We open the simulation, by goto file menu and open simulation option ->Start the simulation
If you face any issues on Simulation of Security Protocol in Contiki, reach us to create an customize Contiki simulation projects.
| Technology | Ph.D | MS | M.Tech |
|---|---|---|---|
| NS2 | 75 | 117 | 95 |
| NS3 | 98 | 119 | 206 |
| OMNET++ | 103 | 95 | 87 |
| OPNET | 36 | 64 | 89 |
| QULANET | 30 | 76 | 60 |
| MININET | 71 | 62 | 74 |
| MATLAB | 96 | 185 | 180 |
| LTESIM | 38 | 32 | 16 |
| COOJA SIMULATOR | 35 | 67 | 28 |
| CONTIKI OS | 42 | 36 | 29 |
| GNS3 | 35 | 89 | 14 |
| NETSIM | 35 | 11 | 21 |
| EVE-NG | 4 | 8 | 9 |
| TRANS | 9 | 5 | 4 |
| PEERSIM | 8 | 8 | 12 |
| GLOMOSIM | 6 | 10 | 6 |
| RTOOL | 13 | 15 | 8 |
| KATHARA SHADOW | 9 | 8 | 9 |
| VNX and VNUML | 8 | 7 | 8 |
| WISTAR | 9 | 9 | 8 |
| CNET | 6 | 8 | 4 |
| ESCAPE | 8 | 7 | 9 |
| NETMIRAGE | 7 | 11 | 7 |
| BOSON NETSIM | 6 | 8 | 9 |
| VIRL | 9 | 9 | 8 |
| CISCO PACKET TRACER | 7 | 7 | 10 |
| SWAN | 9 | 19 | 5 |
| JAVASIM | 40 | 68 | 69 |
| SSFNET | 7 | 9 | 8 |
| TOSSIM | 5 | 7 | 4 |
| PSIM | 7 | 8 | 6 |
| PETRI NET | 4 | 6 | 4 |
| ONESIM | 5 | 10 | 5 |
| OPTISYSTEM | 32 | 64 | 24 |
| DIVERT | 4 | 9 | 8 |
| TINY OS | 19 | 27 | 17 |
| TRANS | 7 | 8 | 6 |
| OPENPANA | 8 | 9 | 9 |
| SECURE CRT | 7 | 8 | 7 |
| EXTENDSIM | 6 | 7 | 5 |
| CONSELF | 7 | 19 | 6 |
| ARENA | 5 | 12 | 9 |
| VENSIM | 8 | 10 | 7 |
| MARIONNET | 5 | 7 | 9 |
| NETKIT | 6 | 8 | 7 |
| GEOIP | 9 | 17 | 8 |
| REAL | 7 | 5 | 5 |
| NEST | 5 | 10 | 9 |
| PTOLEMY | 7 | 8 | 4 |