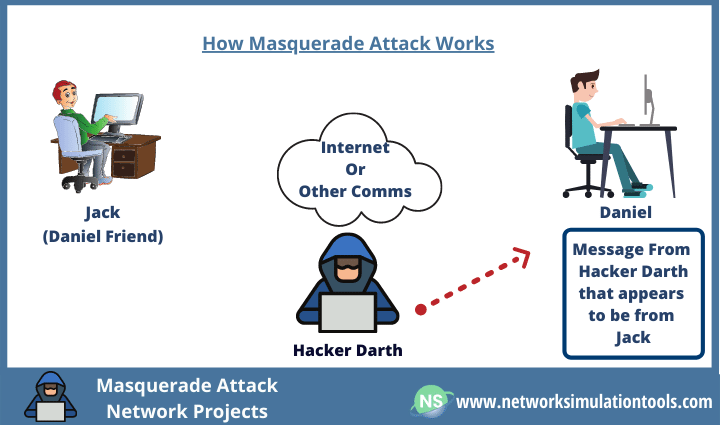
Masquerade Attack Network Projects will control the access for malicious entry in the networks. A masquerade attack is an active attack that uses fake identities like network ID to get unauthorized access to personal data by legitimate identity. That is to say, it spoofs the identity to take part in the network. In that, the spoofing identity may be IP address, MAC address, ID, and so on.
Though it launches in a number of forms like DHCP, Spoofing, and so on, insider attack is the most general. In detail, an insider can get access to another worker’s system by spoofing. In this case, the insider takes in malicious activity by hiding in the victim’s identity. As well, VANET, MANET, IoT 5G, SDN are also at risk of this attack. Thus, the Detection of this network attack is a little difficult. In down, we plotted notable ideas for your note.
Of course, there are several methods; still, it needs advances. For a case in point, RSSI-based attack detection shows well accuracy. On the other hand, it demands large instances of RSSI that makes it complex. In this way, each method has pros and cons.
In addition to the above methods, Trust Computation, Node Direction, and Position Control are also notable methods. On these ideas, we frame our concept by novel algorithms. At present, AI is useful for Masquerade Attack Network Projects. Thus, we are also working towards this fact. As a matter of fact, we have depth wisdom in other kinds of attacks too.
If your field is network security, then do your project under this attack. Yet, it needs great expertise. Don’t get worried as we have 100+ experts who have wide insights. We first give you an outline of the ideas with phd projects in network engineering. Then, we guide you until the project finishing point. In this way, we treat each of our clients to make them masters. On the whole, you will have a fine project with apt yields. To end this, our brainy mind will uplift your thoughts. Let’s work together for you.
| Technology | Ph.D | MS | M.Tech |
|---|---|---|---|
| NS2 | 75 | 117 | 95 |
| NS3 | 98 | 119 | 206 |
| OMNET++ | 103 | 95 | 87 |
| OPNET | 36 | 64 | 89 |
| QULANET | 30 | 76 | 60 |
| MININET | 71 | 62 | 74 |
| MATLAB | 96 | 185 | 180 |
| LTESIM | 38 | 32 | 16 |
| COOJA SIMULATOR | 35 | 67 | 28 |
| CONTIKI OS | 42 | 36 | 29 |
| GNS3 | 35 | 89 | 14 |
| NETSIM | 35 | 11 | 21 |
| EVE-NG | 4 | 8 | 9 |
| TRANS | 9 | 5 | 4 |
| PEERSIM | 8 | 8 | 12 |
| GLOMOSIM | 6 | 10 | 6 |
| RTOOL | 13 | 15 | 8 |
| KATHARA SHADOW | 9 | 8 | 9 |
| VNX and VNUML | 8 | 7 | 8 |
| WISTAR | 9 | 9 | 8 |
| CNET | 6 | 8 | 4 |
| ESCAPE | 8 | 7 | 9 |
| NETMIRAGE | 7 | 11 | 7 |
| BOSON NETSIM | 6 | 8 | 9 |
| VIRL | 9 | 9 | 8 |
| CISCO PACKET TRACER | 7 | 7 | 10 |
| SWAN | 9 | 19 | 5 |
| JAVASIM | 40 | 68 | 69 |
| SSFNET | 7 | 9 | 8 |
| TOSSIM | 5 | 7 | 4 |
| PSIM | 7 | 8 | 6 |
| PETRI NET | 4 | 6 | 4 |
| ONESIM | 5 | 10 | 5 |
| OPTISYSTEM | 32 | 64 | 24 |
| DIVERT | 4 | 9 | 8 |
| TINY OS | 19 | 27 | 17 |
| TRANS | 7 | 8 | 6 |
| OPENPANA | 8 | 9 | 9 |
| SECURE CRT | 7 | 8 | 7 |
| EXTENDSIM | 6 | 7 | 5 |
| CONSELF | 7 | 19 | 6 |
| ARENA | 5 | 12 | 9 |
| VENSIM | 8 | 10 | 7 |
| MARIONNET | 5 | 7 | 9 |
| NETKIT | 6 | 8 | 7 |
| GEOIP | 9 | 17 | 8 |
| REAL | 7 | 5 | 5 |
| NEST | 5 | 10 | 9 |
| PTOLEMY | 7 | 8 | 4 |