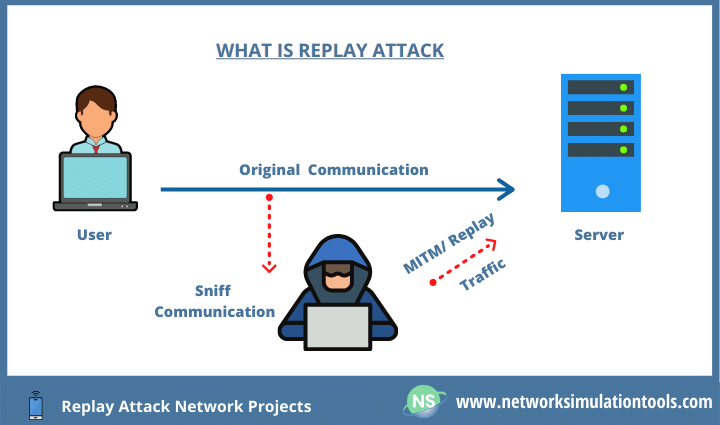
Replay Attack Network Projects mean to safeguard the networks in any hard environs. To begin with this, Replay Attack that is a Playback attack refers to the repeated or delayed use of valid transmission in the network. To be clear, the attacker sniffs the data transmitted between two nodes. Then, the attacker uses this data at another time. In most cases, security credentials like Password, Secret Key are vulnerable to this attack.
In core, Replay Attack Network Projects focuses on both Security Credentials as well as Routing Messages. For a case, a reactive protocol such as AODV is open to this attack. To tell the truth, the Replay attack is the form of a Man-In-The-Middle attack. It is a mandate to mitigate this attack since it extends its exposure in real-world use cases too. For example IoV, smart homes, keyless vehicles, and so on.
Secure Key Exchange and so on. At first, frequency variation and hopping detect the replay attacks. Then, any of the above methods mitigate the attack. At this point, the main issue comes. As we all know, most of the network entities have some degree of resources. That is to say; lightweight mechanisms are most apt for Replay Attack Network Projects. Here, we offered a list of notable algorithms.
Besides to above methods, hardware-based security such as PUF authentication is also the finest solution. Thus, the current studies are ongoing in this area too. To mention that, we have a team of experts with extensive skills in this field.
We have tons of real-time ideas to do your project in any networking field. We know that your needs may vary all the time. That’s why we lend our help as much as flexible for PhD research topics in computer networking. You can learn all the things from us. Our 18+ years of practice will be the base for you. In any of that, we offer all in all services. To end this, you can grab them by just hit it off a mail to us. What’s more, you need it? Hold your work with us.
| Technology | Ph.D | MS | M.Tech |
|---|---|---|---|
| NS2 | 75 | 117 | 95 |
| NS3 | 98 | 119 | 206 |
| OMNET++ | 103 | 95 | 87 |
| OPNET | 36 | 64 | 89 |
| QULANET | 30 | 76 | 60 |
| MININET | 71 | 62 | 74 |
| MATLAB | 96 | 185 | 180 |
| LTESIM | 38 | 32 | 16 |
| COOJA SIMULATOR | 35 | 67 | 28 |
| CONTIKI OS | 42 | 36 | 29 |
| GNS3 | 35 | 89 | 14 |
| NETSIM | 35 | 11 | 21 |
| EVE-NG | 4 | 8 | 9 |
| TRANS | 9 | 5 | 4 |
| PEERSIM | 8 | 8 | 12 |
| GLOMOSIM | 6 | 10 | 6 |
| RTOOL | 13 | 15 | 8 |
| KATHARA SHADOW | 9 | 8 | 9 |
| VNX and VNUML | 8 | 7 | 8 |
| WISTAR | 9 | 9 | 8 |
| CNET | 6 | 8 | 4 |
| ESCAPE | 8 | 7 | 9 |
| NETMIRAGE | 7 | 11 | 7 |
| BOSON NETSIM | 6 | 8 | 9 |
| VIRL | 9 | 9 | 8 |
| CISCO PACKET TRACER | 7 | 7 | 10 |
| SWAN | 9 | 19 | 5 |
| JAVASIM | 40 | 68 | 69 |
| SSFNET | 7 | 9 | 8 |
| TOSSIM | 5 | 7 | 4 |
| PSIM | 7 | 8 | 6 |
| PETRI NET | 4 | 6 | 4 |
| ONESIM | 5 | 10 | 5 |
| OPTISYSTEM | 32 | 64 | 24 |
| DIVERT | 4 | 9 | 8 |
| TINY OS | 19 | 27 | 17 |
| TRANS | 7 | 8 | 6 |
| OPENPANA | 8 | 9 | 9 |
| SECURE CRT | 7 | 8 | 7 |
| EXTENDSIM | 6 | 7 | 5 |
| CONSELF | 7 | 19 | 6 |
| ARENA | 5 | 12 | 9 |
| VENSIM | 8 | 10 | 7 |
| MARIONNET | 5 | 7 | 9 |
| NETKIT | 6 | 8 | 7 |
| GEOIP | 9 | 17 | 8 |
| REAL | 7 | 5 | 5 |
| NEST | 5 | 10 | 9 |
| PTOLEMY | 7 | 8 | 4 |