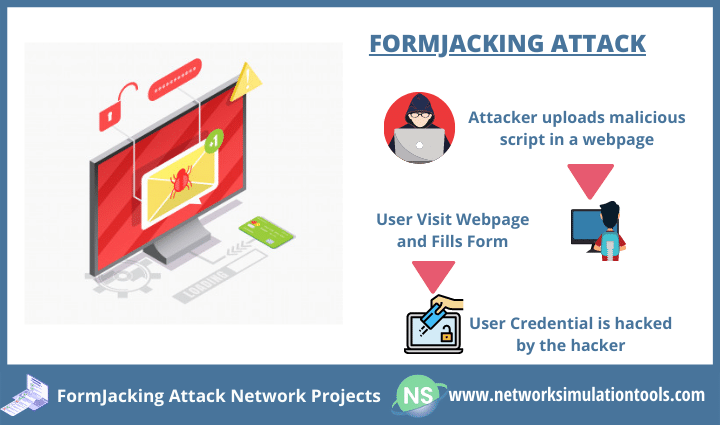
Formjacking Attack Network Projects send you the defense scheme to win from an attack. A title that forms jacking is a new form of cyberattack in which user’s personal info has hacked by the attackers. There are certain risks by this attack, namely, spoofing identity and loss of reputation.
Let’s think why form jacking on the growth is? As a rise of online forms submission, attackers inject the Javascript code as easier. When attackers compromise it, it is each deal with the complete transaction. For instance, the attacker will hack the user’s payment details. If you are looking for an interesting way to detect or prevent such Network attacks, check out this post for the great info as we are the solution for addressing this kind of attack.
The most important way for attackers to steal the data and perform code injection is to use Digital Payment Card Skimming (DPCS). It is good to have some methods of detection. From a full survey, we find some methods.
Bullying is not going to go away. Attackers strengthen day by day. It is not an easy way to prevent this attack. It requires more robust ways and means to solve it. Since it happens in more places, we cannot handle it by a single and also simple method. So prevention is better than cure. Now and then, we can use prevention way instead of suffering from threats. You can have a view on some prevention ways.
In general, we need some fresh ideas for developing a new project with PhD guidance in digital forensics. If you would know the value of trendy ideas, come and try with our ideas as follows.
We hope that this info is Formjacking Attack Network Projects helps out for you, and you can get started of form jacking attacks network projects. We keep up the great work that’s more high quality.
| Technology | Ph.D | MS | M.Tech |
|---|---|---|---|
| NS2 | 75 | 117 | 95 |
| NS3 | 98 | 119 | 206 |
| OMNET++ | 103 | 95 | 87 |
| OPNET | 36 | 64 | 89 |
| QULANET | 30 | 76 | 60 |
| MININET | 71 | 62 | 74 |
| MATLAB | 96 | 185 | 180 |
| LTESIM | 38 | 32 | 16 |
| COOJA SIMULATOR | 35 | 67 | 28 |
| CONTIKI OS | 42 | 36 | 29 |
| GNS3 | 35 | 89 | 14 |
| NETSIM | 35 | 11 | 21 |
| EVE-NG | 4 | 8 | 9 |
| TRANS | 9 | 5 | 4 |
| PEERSIM | 8 | 8 | 12 |
| GLOMOSIM | 6 | 10 | 6 |
| RTOOL | 13 | 15 | 8 |
| KATHARA SHADOW | 9 | 8 | 9 |
| VNX and VNUML | 8 | 7 | 8 |
| WISTAR | 9 | 9 | 8 |
| CNET | 6 | 8 | 4 |
| ESCAPE | 8 | 7 | 9 |
| NETMIRAGE | 7 | 11 | 7 |
| BOSON NETSIM | 6 | 8 | 9 |
| VIRL | 9 | 9 | 8 |
| CISCO PACKET TRACER | 7 | 7 | 10 |
| SWAN | 9 | 19 | 5 |
| JAVASIM | 40 | 68 | 69 |
| SSFNET | 7 | 9 | 8 |
| TOSSIM | 5 | 7 | 4 |
| PSIM | 7 | 8 | 6 |
| PETRI NET | 4 | 6 | 4 |
| ONESIM | 5 | 10 | 5 |
| OPTISYSTEM | 32 | 64 | 24 |
| DIVERT | 4 | 9 | 8 |
| TINY OS | 19 | 27 | 17 |
| TRANS | 7 | 8 | 6 |
| OPENPANA | 8 | 9 | 9 |
| SECURE CRT | 7 | 8 | 7 |
| EXTENDSIM | 6 | 7 | 5 |
| CONSELF | 7 | 19 | 6 |
| ARENA | 5 | 12 | 9 |
| VENSIM | 8 | 10 | 7 |
| MARIONNET | 5 | 7 | 9 |
| NETKIT | 6 | 8 | 7 |
| GEOIP | 9 | 17 | 8 |
| REAL | 7 | 5 | 5 |
| NEST | 5 | 10 | 9 |
| PTOLEMY | 7 | 8 | 4 |