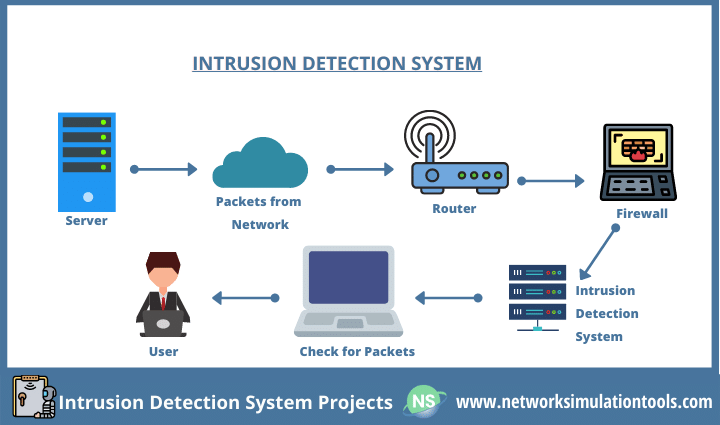
Intrusion Detection System Projects are always palatable to target attackers in the whole system. An intrusion detection system is a security scheme that purpose is to find malicious activity from false alarms. The intrusion detection system is mean to IDS. There are three types of intruders, such as Clandestine, Masquerader, and also Misfeasor. Certain behaviors of intruders are,
Right now, IDS is a stand that acts as a security solution. Thus, it connects the security researchers to the IDS. Also, this field is a classic one among all stream of students. Before knowing how to start a project, it’s needed to check out the IDS classes at first.
In the context of IDS, quite a lot of fields are working early and now. For instance, a wireless network is a field that needs IDS while transmitting packets from one place to another. In this case, a deep packet inspection (DPI) method is now useful to look at important features of the packet stream.
A lack of security leads to more issues. Often, there are various issues unsolved in IDS. It is all the time hard to avoid those issues of it. With attention to security, it must avoid as much as possible when using any method.
Another key point to work on the IDS project is a method. We have a new set of ways to hunt against attackers. In other words, machine learning is a fast way to detect intrusions. We list out such fast and latest methods for you in the following with PhD guidance in pattern analysis and machine intelligence. To implement your IDS projects, you can prefer any method.
Along with the above methods, it is open to learning all other IDS methods. For that reason, we introduce all such methods for you below. At the same time, we handle any recent topics or methods in this IDS area.
In general, creativity always limits by constraints. So the visions to be clear before work it. On the other hand, it is hard to be fully keeping an eye on the constraints of IDS. Effective IDS must meet the following constraints.
We foresee the main aspects of IDS and its need in the upcoming years. All in all, intrusion detection system projects are a great chance for final year students and research scholars.
| Technology | Ph.D | MS | M.Tech |
|---|---|---|---|
| NS2 | 75 | 117 | 95 |
| NS3 | 98 | 119 | 206 |
| OMNET++ | 103 | 95 | 87 |
| OPNET | 36 | 64 | 89 |
| QULANET | 30 | 76 | 60 |
| MININET | 71 | 62 | 74 |
| MATLAB | 96 | 185 | 180 |
| LTESIM | 38 | 32 | 16 |
| COOJA SIMULATOR | 35 | 67 | 28 |
| CONTIKI OS | 42 | 36 | 29 |
| GNS3 | 35 | 89 | 14 |
| NETSIM | 35 | 11 | 21 |
| EVE-NG | 4 | 8 | 9 |
| TRANS | 9 | 5 | 4 |
| PEERSIM | 8 | 8 | 12 |
| GLOMOSIM | 6 | 10 | 6 |
| RTOOL | 13 | 15 | 8 |
| KATHARA SHADOW | 9 | 8 | 9 |
| VNX and VNUML | 8 | 7 | 8 |
| WISTAR | 9 | 9 | 8 |
| CNET | 6 | 8 | 4 |
| ESCAPE | 8 | 7 | 9 |
| NETMIRAGE | 7 | 11 | 7 |
| BOSON NETSIM | 6 | 8 | 9 |
| VIRL | 9 | 9 | 8 |
| CISCO PACKET TRACER | 7 | 7 | 10 |
| SWAN | 9 | 19 | 5 |
| JAVASIM | 40 | 68 | 69 |
| SSFNET | 7 | 9 | 8 |
| TOSSIM | 5 | 7 | 4 |
| PSIM | 7 | 8 | 6 |
| PETRI NET | 4 | 6 | 4 |
| ONESIM | 5 | 10 | 5 |
| OPTISYSTEM | 32 | 64 | 24 |
| DIVERT | 4 | 9 | 8 |
| TINY OS | 19 | 27 | 17 |
| TRANS | 7 | 8 | 6 |
| OPENPANA | 8 | 9 | 9 |
| SECURE CRT | 7 | 8 | 7 |
| EXTENDSIM | 6 | 7 | 5 |
| CONSELF | 7 | 19 | 6 |
| ARENA | 5 | 12 | 9 |
| VENSIM | 8 | 10 | 7 |
| MARIONNET | 5 | 7 | 9 |
| NETKIT | 6 | 8 | 7 |
| GEOIP | 9 | 17 | 8 |
| REAL | 7 | 5 | 5 |
| NEST | 5 | 10 | 9 |
| PTOLEMY | 7 | 8 | 4 |