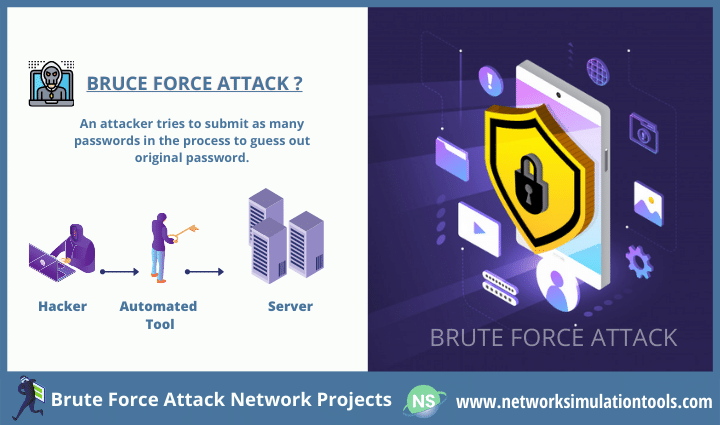
Brute Force Attack Network Projects deal with the central cryptanalysis attack’s overall networks. Brute force aims to breach the security of any cryptography algorithm. In this attack, the attacker submits many passwords or phrases to crack the security in a trial and error manner. The fact is that anyone of these passwords will work. On the one hand, this type of password guessing allows unauthorized access. On the other hand, key guessing also carries over the system. Henceforth, the attacker can derive the key used for security.
We tend to start with the types of brute force attacks. Of course, it has a number of types that carry on any kind of network like SDN, NDN, NFV, WSN, MANET, and so on. The central types of brute force attack are,
Most of the Brute Force Attack Network Projects use random number generators to launch this attack. For that, the custom hardware like FPGA, ASIC generates random passwords and keys. Besides, some software also allows brute force attacks. They are,
Over the iteration, the attacker will have the key or password. To be sure, this is a basic and widely used method as we all know that the strong key will have a large key length. This is because the brute force attack has an exponential relation with the key length. That is to say; it needs large resources to crack the large keys. Thus, modern systems use large size keys.
In all of the major cryptosystems, brute force plays a vital role. Of course, the time taken by this attack to crack the secret key will reveal the strength of that algorithm. Thus, Brute Force Attack Network Projects act as an auxiliary for all network security projects. For a case in point, we provided a few of the notable crypto algorithms that use Brute Force as an evaluation criterion.
And more to mention, whenever we use the above algorithms, we also enable brute force evaluation. On the positive side, it shows efficacy. Often, Hybrid Algorithms are also the best solution to cope with the brute force attack. Such algorithms include ECC with RSA, AES-DES, and so on. Apart from this, a strong key generation (within a key length bound) reflect an optimization problem. Yes, most of the time, we generate optimal keys to defend against brute force attack using latest cyber attack simulation software.
At any time, you can hit our door to grab exciting stuff. We have a smart team of techies, developers, and reviewers to endow a unique project. Our team will put their brain in each nook of the project. By means all, you will grab first grades without a doubt. In a word, join us to have a superb career ahead.
| Technology | Ph.D | MS | M.Tech |
|---|---|---|---|
| NS2 | 75 | 117 | 95 |
| NS3 | 98 | 119 | 206 |
| OMNET++ | 103 | 95 | 87 |
| OPNET | 36 | 64 | 89 |
| QULANET | 30 | 76 | 60 |
| MININET | 71 | 62 | 74 |
| MATLAB | 96 | 185 | 180 |
| LTESIM | 38 | 32 | 16 |
| COOJA SIMULATOR | 35 | 67 | 28 |
| CONTIKI OS | 42 | 36 | 29 |
| GNS3 | 35 | 89 | 14 |
| NETSIM | 35 | 11 | 21 |
| EVE-NG | 4 | 8 | 9 |
| TRANS | 9 | 5 | 4 |
| PEERSIM | 8 | 8 | 12 |
| GLOMOSIM | 6 | 10 | 6 |
| RTOOL | 13 | 15 | 8 |
| KATHARA SHADOW | 9 | 8 | 9 |
| VNX and VNUML | 8 | 7 | 8 |
| WISTAR | 9 | 9 | 8 |
| CNET | 6 | 8 | 4 |
| ESCAPE | 8 | 7 | 9 |
| NETMIRAGE | 7 | 11 | 7 |
| BOSON NETSIM | 6 | 8 | 9 |
| VIRL | 9 | 9 | 8 |
| CISCO PACKET TRACER | 7 | 7 | 10 |
| SWAN | 9 | 19 | 5 |
| JAVASIM | 40 | 68 | 69 |
| SSFNET | 7 | 9 | 8 |
| TOSSIM | 5 | 7 | 4 |
| PSIM | 7 | 8 | 6 |
| PETRI NET | 4 | 6 | 4 |
| ONESIM | 5 | 10 | 5 |
| OPTISYSTEM | 32 | 64 | 24 |
| DIVERT | 4 | 9 | 8 |
| TINY OS | 19 | 27 | 17 |
| TRANS | 7 | 8 | 6 |
| OPENPANA | 8 | 9 | 9 |
| SECURE CRT | 7 | 8 | 7 |
| EXTENDSIM | 6 | 7 | 5 |
| CONSELF | 7 | 19 | 6 |
| ARENA | 5 | 12 | 9 |
| VENSIM | 8 | 10 | 7 |
| MARIONNET | 5 | 7 | 9 |
| NETKIT | 6 | 8 | 7 |
| GEOIP | 9 | 17 | 8 |
| REAL | 7 | 5 | 5 |
| NEST | 5 | 10 | 9 |
| PTOLEMY | 7 | 8 | 4 |