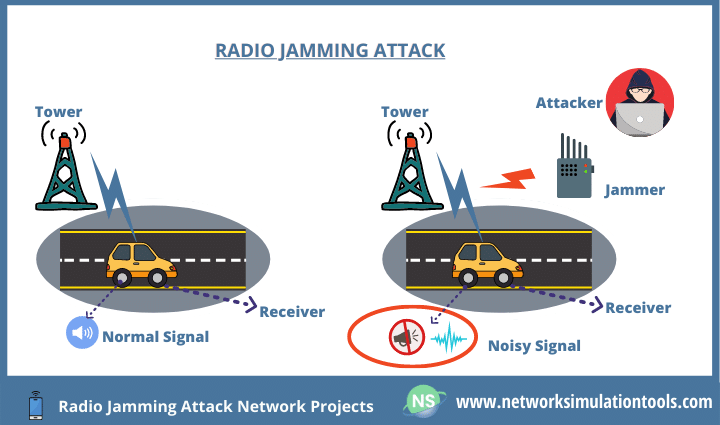
Radio Jamming Attack Network Projects eliminate interference between source and destination since Radio Jamming disrupts the legitimate data transmission by sending unwanted signals that are jamming signals. In broad, the major idea behind this attack is ‘Reducing SNR’ of the legitimate signals. As a result, the destination receives a corrupted or noisy signal. As a matter of fact, the destination will be unable to gather info from that signal.
Yes, Radio Jamming Attack Network Projects work upon a number of types. So far, it has the following types as,
Deceptive Jamming and so as well, the attack runs on the reactive and proactive manners too. In any network, the jamming attack takes off. For a case in point, WSN, CRN, MANET, FANET, ICN, and so on are some of them. Most importantly, CRN is at most risk of this attack. We guide you to implement phd research topics in wireless sensor network. Since it already has high interference between users. By adding up the jamming signal, it worsens the network efficiency. All in all, it is predominant to detect and mitigate this attack.
The first and foremost method to detect this attack is the use of RSSI and SNR. As its nature is to disrupt the data, it is easy but effective too. However, nowadays, the attacker triggers more potent attacks. To cope with such attacks, recent works put effort on detection methods.
Well, now, it is time to alleviate the attack. The most common anti-jamming method is to interfere with the jamming signals by other signals like in honeypots. As it has some cost limits, there are some other techs that are open to exploring.
We hope that all the above info will open up your project. To tell the truth, we have 1000+ fresh ideas for you. On top of, we get this info only from high-rate journals like IEEE. To do so, we have a keen team for new updates in this field. So far, we lent 52+ themes for our happiest students. If you are eager to become one among them, then just knock our mail. We will get back to you as per your ease time. To sum up, there is no bound to limit your success when you have our vast support.
| Technology | Ph.D | MS | M.Tech |
|---|---|---|---|
| NS2 | 75 | 117 | 95 |
| NS3 | 98 | 119 | 206 |
| OMNET++ | 103 | 95 | 87 |
| OPNET | 36 | 64 | 89 |
| QULANET | 30 | 76 | 60 |
| MININET | 71 | 62 | 74 |
| MATLAB | 96 | 185 | 180 |
| LTESIM | 38 | 32 | 16 |
| COOJA SIMULATOR | 35 | 67 | 28 |
| CONTIKI OS | 42 | 36 | 29 |
| GNS3 | 35 | 89 | 14 |
| NETSIM | 35 | 11 | 21 |
| EVE-NG | 4 | 8 | 9 |
| TRANS | 9 | 5 | 4 |
| PEERSIM | 8 | 8 | 12 |
| GLOMOSIM | 6 | 10 | 6 |
| RTOOL | 13 | 15 | 8 |
| KATHARA SHADOW | 9 | 8 | 9 |
| VNX and VNUML | 8 | 7 | 8 |
| WISTAR | 9 | 9 | 8 |
| CNET | 6 | 8 | 4 |
| ESCAPE | 8 | 7 | 9 |
| NETMIRAGE | 7 | 11 | 7 |
| BOSON NETSIM | 6 | 8 | 9 |
| VIRL | 9 | 9 | 8 |
| CISCO PACKET TRACER | 7 | 7 | 10 |
| SWAN | 9 | 19 | 5 |
| JAVASIM | 40 | 68 | 69 |
| SSFNET | 7 | 9 | 8 |
| TOSSIM | 5 | 7 | 4 |
| PSIM | 7 | 8 | 6 |
| PETRI NET | 4 | 6 | 4 |
| ONESIM | 5 | 10 | 5 |
| OPTISYSTEM | 32 | 64 | 24 |
| DIVERT | 4 | 9 | 8 |
| TINY OS | 19 | 27 | 17 |
| TRANS | 7 | 8 | 6 |
| OPENPANA | 8 | 9 | 9 |
| SECURE CRT | 7 | 8 | 7 |
| EXTENDSIM | 6 | 7 | 5 |
| CONSELF | 7 | 19 | 6 |
| ARENA | 5 | 12 | 9 |
| VENSIM | 8 | 10 | 7 |
| MARIONNET | 5 | 7 | 9 |
| NETKIT | 6 | 8 | 7 |
| GEOIP | 9 | 17 | 8 |
| REAL | 7 | 5 | 5 |
| NEST | 5 | 10 | 9 |
| PTOLEMY | 7 | 8 | 4 |