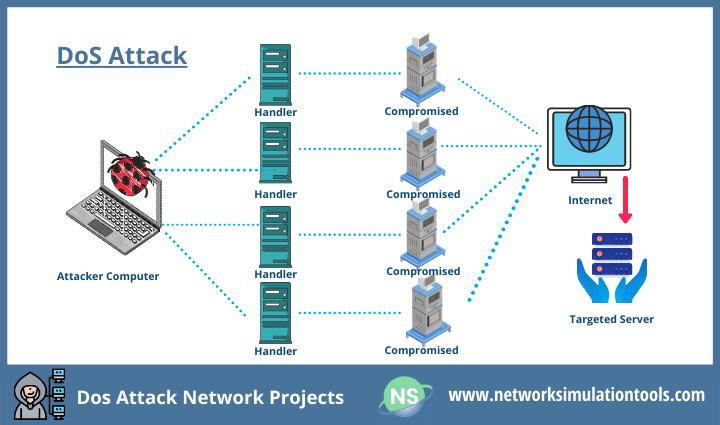
DoS Attack Network Projects facilitate high-level security in the networks. The term DoS stands for Denial of Service, which is the form of a flooding attack. In DoS, the attacker used to send unwanted packets to a particular victim node continuously. On the one hand, the victim gains nothing from these unwanted packets. On the other hand, the victim service becomes unavailable for all other legitimate nodes in the network. On the whole, it consumes the network resources and degrades the performance.
In the point of truth, DoS attacker takes off the attack in any network environment, probably at the application layer. All of the networks, including SDN, NDN, MANET, UAV, PhD VANET Projects, IoT, and WSN, are at high risk on DoS. As well, Cellular networks such as LTE, LTE-A, and 5G are also the targets of DoS. In precise, Cloud-RAN and Fog-RAN are vulnerable to DoS attacks. To do a DoS Attack Network Project, it is crucial to know the way of DoS. To be sure, DoS takes any of the following forms.
OS-based Attacks and moreApart from the variants, DoS can either be Active or Passive, Local or Extended and Malicious or Rational. It also brings in a cooperative manner that is to say as Distributed DoS (DDoS). As it varies its features and faces, it is tough to detect the DoS accurately. Yet, DoS detection is in the first place of on-going Network research topics under network security.
In the above techniques, ML and DL methods inspect the data packets in deep. Then, it classifies the attacks as per the IP packet features. For instance, the DoS attack has a different pattern in Src_IP, Dst_IP, Src_MAC, Dst_MAC, and so on. Likewise, there are many features nearly 40+. On the deep inspection, these methods identify the attackers. In the second place, we need to go with DoS mitigation.
Of course, these methods work after the Detection of the attack. There is also a way to get rid of the DoS attack that is DoS Prevention policies. In actuality, DoS prevention relates to SLA agreements. As well, IP blocking, access control are also key prevention methods. This or that, it is good to have a special Detection, Mitigation, and Prevention policies for your DoS Attack Network Projects.
To conclude this, we like to tell the fact that DoS based projects are the first in the research race. If you want to kick your work, then do it with us. In detail, we offer upright help in all aspects for you. Our smart teamwork on your project will surely reflect as a huge feat. To be best in your field, then you must have more than enough exposure in that. When you have no way to enlarge your view, then join us now. Soon, you will get all you need in your field.
| Technology | Ph.D | MS | M.Tech |
|---|---|---|---|
| NS2 | 75 | 117 | 95 |
| NS3 | 98 | 119 | 206 |
| OMNET++ | 103 | 95 | 87 |
| OPNET | 36 | 64 | 89 |
| QULANET | 30 | 76 | 60 |
| MININET | 71 | 62 | 74 |
| MATLAB | 96 | 185 | 180 |
| LTESIM | 38 | 32 | 16 |
| COOJA SIMULATOR | 35 | 67 | 28 |
| CONTIKI OS | 42 | 36 | 29 |
| GNS3 | 35 | 89 | 14 |
| NETSIM | 35 | 11 | 21 |
| EVE-NG | 4 | 8 | 9 |
| TRANS | 9 | 5 | 4 |
| PEERSIM | 8 | 8 | 12 |
| GLOMOSIM | 6 | 10 | 6 |
| RTOOL | 13 | 15 | 8 |
| KATHARA SHADOW | 9 | 8 | 9 |
| VNX and VNUML | 8 | 7 | 8 |
| WISTAR | 9 | 9 | 8 |
| CNET | 6 | 8 | 4 |
| ESCAPE | 8 | 7 | 9 |
| NETMIRAGE | 7 | 11 | 7 |
| BOSON NETSIM | 6 | 8 | 9 |
| VIRL | 9 | 9 | 8 |
| CISCO PACKET TRACER | 7 | 7 | 10 |
| SWAN | 9 | 19 | 5 |
| JAVASIM | 40 | 68 | 69 |
| SSFNET | 7 | 9 | 8 |
| TOSSIM | 5 | 7 | 4 |
| PSIM | 7 | 8 | 6 |
| PETRI NET | 4 | 6 | 4 |
| ONESIM | 5 | 10 | 5 |
| OPTISYSTEM | 32 | 64 | 24 |
| DIVERT | 4 | 9 | 8 |
| TINY OS | 19 | 27 | 17 |
| TRANS | 7 | 8 | 6 |
| OPENPANA | 8 | 9 | 9 |
| SECURE CRT | 7 | 8 | 7 |
| EXTENDSIM | 6 | 7 | 5 |
| CONSELF | 7 | 19 | 6 |
| ARENA | 5 | 12 | 9 |
| VENSIM | 8 | 10 | 7 |
| MARIONNET | 5 | 7 | 9 |
| NETKIT | 6 | 8 | 7 |
| GEOIP | 9 | 17 | 8 |
| REAL | 7 | 5 | 5 |
| NEST | 5 | 10 | 9 |
| PTOLEMY | 7 | 8 | 4 |