Wormhole Attack Network Projects are a powerful way to defend against tunneled wormhole. In general, wormhole carries by two or more attackers. An attacker from a place of the network tunnels a legitimate packet to another attacker in the same network. For tunneling, it uses wireless or wired links. In most of the cases, the wormhole carries single-hop transmission. Owing to its connection, it has two types as in-band and also out-of-band wormhole.
At the Time data reaches another attacker node, then the entire network becomes at the risk of a Replay attack. Yes, the malicious node uses the tunneled data to launch a replay attack. On common, WSN and ad-hoc networks are at the utmost risk of the wormhole. The main reason is that it affects the network routing in particularly ad-hoc protocols like AODV. After that, it launches the many other attacks on routing. That is to say, doing Wormhole Attack Projects leads to myriad benefits.
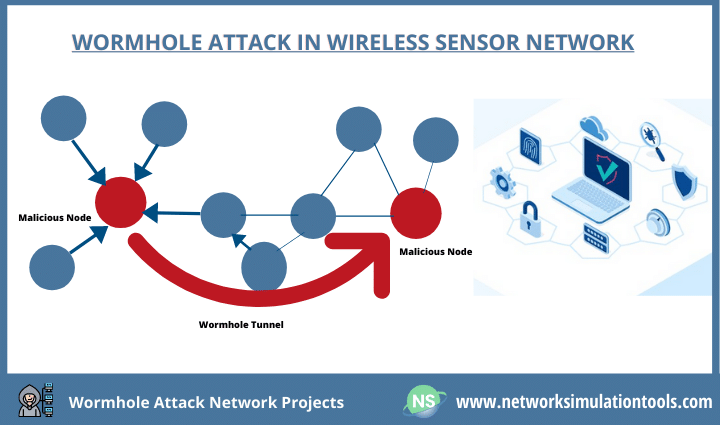
At this Time, Machine Learning and Deep Learning methods are there for defending wormholes attack. At length, these methods classify the nodes as Normal and Malicious. For that, it depends upon the IP packet features, Energy model of the nodes, and Power ratio of the links. To be sure, the power ratio of the tunneled link is always high. Once we detected the malicious nodes, and then it is easy to isolate them. On the whole, we are also moving towards ML and DL techs in order to pledge fine quality.
In sum, you can grasp any novel idea from us, even with a single mail. We never force you to pick our thoughts. Instead, we first give you a list of novel topics with phd research guidance. Then, we filter them upon your interest along with you. From that, we guide you to opt for your topic. In the same way, we have discussions with you at all stages of the work so that you will able to closely track your work online or offline.
| Technology | Ph.D | MS | M.Tech |
|---|---|---|---|
| NS2 | 75 | 117 | 95 |
| NS3 | 98 | 119 | 206 |
| OMNET++ | 103 | 95 | 87 |
| OPNET | 36 | 64 | 89 |
| QULANET | 30 | 76 | 60 |
| MININET | 71 | 62 | 74 |
| MATLAB | 96 | 185 | 180 |
| LTESIM | 38 | 32 | 16 |
| COOJA SIMULATOR | 35 | 67 | 28 |
| CONTIKI OS | 42 | 36 | 29 |
| GNS3 | 35 | 89 | 14 |
| NETSIM | 35 | 11 | 21 |
| EVE-NG | 4 | 8 | 9 |
| TRANS | 9 | 5 | 4 |
| PEERSIM | 8 | 8 | 12 |
| GLOMOSIM | 6 | 10 | 6 |
| RTOOL | 13 | 15 | 8 |
| KATHARA SHADOW | 9 | 8 | 9 |
| VNX and VNUML | 8 | 7 | 8 |
| WISTAR | 9 | 9 | 8 |
| CNET | 6 | 8 | 4 |
| ESCAPE | 8 | 7 | 9 |
| NETMIRAGE | 7 | 11 | 7 |
| BOSON NETSIM | 6 | 8 | 9 |
| VIRL | 9 | 9 | 8 |
| CISCO PACKET TRACER | 7 | 7 | 10 |
| SWAN | 9 | 19 | 5 |
| JAVASIM | 40 | 68 | 69 |
| SSFNET | 7 | 9 | 8 |
| TOSSIM | 5 | 7 | 4 |
| PSIM | 7 | 8 | 6 |
| PETRI NET | 4 | 6 | 4 |
| ONESIM | 5 | 10 | 5 |
| OPTISYSTEM | 32 | 64 | 24 |
| DIVERT | 4 | 9 | 8 |
| TINY OS | 19 | 27 | 17 |
| TRANS | 7 | 8 | 6 |
| OPENPANA | 8 | 9 | 9 |
| SECURE CRT | 7 | 8 | 7 |
| EXTENDSIM | 6 | 7 | 5 |
| CONSELF | 7 | 19 | 6 |
| ARENA | 5 | 12 | 9 |
| VENSIM | 8 | 10 | 7 |
| MARIONNET | 5 | 7 | 9 |
| NETKIT | 6 | 8 | 7 |
| GEOIP | 9 | 17 | 8 |
| REAL | 7 | 5 | 5 |
| NEST | 5 | 10 | 9 |
| PTOLEMY | 7 | 8 | 4 |